Researchers at MacKeeper have found malicious Google Ads for “Mac cleaner” tools that trick users into running dangerous Terminal commands. Stay safe by learning how to spot these fake Apple sites.
Researchers at MacKeeper have identified malicious Google Ads promoting fake “Mac cleaner” tools that trick users into running dangerous Terminal commands. The campaign directs victims to Apple-lookalike pages designed to gain full control of macOS systems.
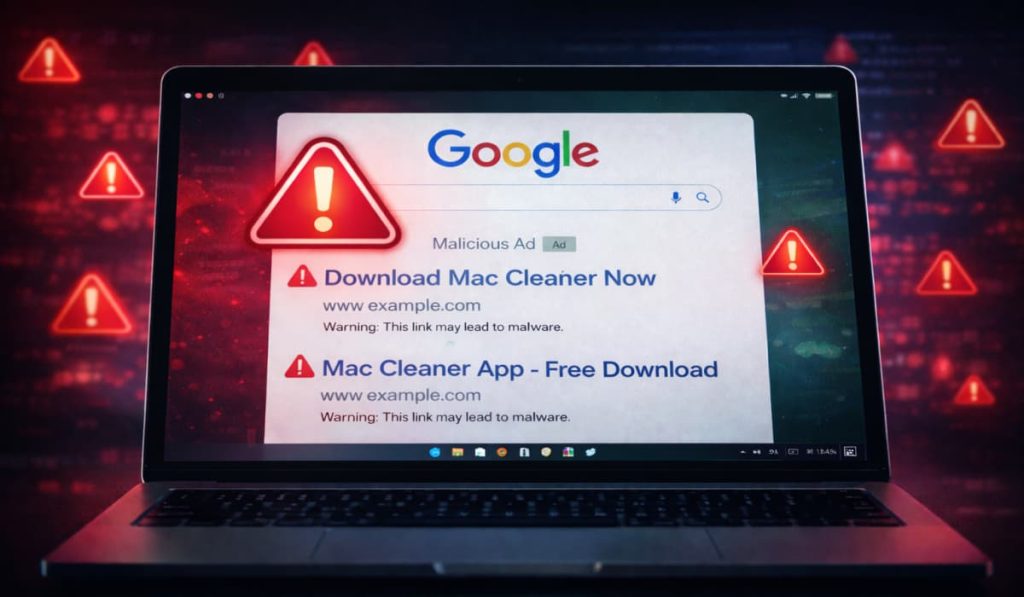
On 26 January 2026, MacKeeper researchers discovered sponsored Google search results targeting users searching for “mac cleaner” utilities. These ads do not provide legitimate cleanup tools. Instead, they redirect users to fraudulent pages that imitate Apple’s official support site and attempt to coerce users into executing malicious commands.
Google Ads often appear at the top of search results, which gives them an implied sense of trust. In this case, the ads led to convincing Apple-style pages hosted through Google-owned services such as docs.google.com and business.google.com, further lowering suspicion.
Once a user lands on the page, they are presented with what appears to be a step-by-step guide for freeing disk space on macOS. The page layout closely resembles Apple’s real support documentation, but key navigation links are nonfunctional.
The core trap is a request to copy and paste a command into macOS Terminal. According to MacKeeper’s research blog post, shared with Hackread.com, the command is obfuscated using Base64 encoding so it appears as unreadable text rather than an obvious system instruction.
When executed, the command decodes the Base64 string and immediately downloads a script from a remote server. That script is then executed with full user permissions. During execution, fake status messages such as “Cleaning macOS Storage” are displayed to reduce suspicion.
Researchers report that this process gives attackers remote control of the affected Mac. From there, attackers can steal sensitive files, extract SSH keys, deploy additional malware, or abuse system resources for activities such as cryptomining.
MacKeeper investigated the advertisers behind the campaign and found that the ads were served through Google-verified accounts. One account was registered under the name Nathaniel Josue Rodriguez, while another was associated with the Aloha Shirt Shop.
According to researchers, both accounts appear to have been compromised rather than created for fraud. The Rodriguez account previously ran normal ads, while the Aloha Shirt Shop account was observed actively serving the malicious Mac cleaner promotion.
This suggests that attackers are hijacking legitimate advertiser accounts to bypass Google’s trust checks and distribute malware using established reputations. MacKeeper has reported the ads to Google in an effort to have them removed.
Your email address will not be published.
Email Address*
FIRSTNAME
LASTNAME
The display of third-party trademarks and trade names on the site do not necessarily indicate any affiliation or endorsement of Hackread.com. If you click an affiliate link and buy a product or service, we may be paid a fee by that merchant.