Cybercriminals have quietly turned Google’s advertising system into a delivery mechanism for malicious code, luring macOS users searching for routine storage fixes into executing obfuscated commands that hand over control of their machines.
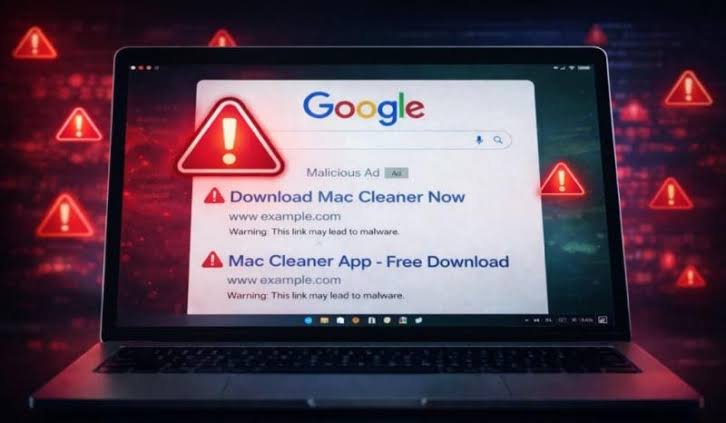
The scheme begins in a familiar place: a Google search. Users typing queries such as “mac cleaner” or “free up disk space” are presented with sponsored results that appear legitimate, sometimes attributed to innocuous-sounding advertisers like “Aloha Shirt Shop” or individuals with long-standing ad histories. These advertisers, researchers say, appear to have been compromised, allowing attackers to exploit the credibility and preferential placement that comes with verified advertising accounts on Google.
Clicking the ad does not lead to a conventional software download. Instead, users are redirected to pages hosted on Google Apps Script domains—addresses that look and feel trustworthy because they sit within Google’s own ecosystem. The pages are styled to resemble Apple’s design language, complete with familiar fonts, layouts and navigation elements that do not actually function. The promise is simple and appealing: a quick way to check storage or clean up a Mac. The mechanism is anything but.
Certified Cyber Crime Investigator Course Launched by Centre for Police Technology
Once on the page, visitors are instructed to open the macOS Terminal and paste a short command. On its surface, the command appears mundane, even reassuring, displaying messages such as “Cleaning macOS Storage…” or “Installing packages please wait…”.
Hidden beneath that text is a Base64-encoded payload. When decoded using the base64 -D flag, the string resolves into a shell command that silently fetches and executes a remote script using tools already present on the system, typically via curl | bash. The technique allows attackers to execute code without leaving obvious files behind, bypassing basic security scanners and relying instead on user trust.
Researchers note that a second, more stealthy variant uses command substitution—$(...)—to decode a concealed URL and immediately pipe its contents into the shell. The effect is the same: remote code execution carried out entirely with the user’s own permissions.
The downloaded scripts, security analysts warn, grant attackers full shell access at the user level. While macOS’s protections limit direct damage to system files, that access is sufficient for a wide range of malicious activity. Scripts observed in the campaign could install persistent malware or adware, harvest browser data and stored credentials, deploy backdoors for remote control, or exfiltrate files to command-and-control servers. Some payloads also include cryptocurrency mining components that quietly consume system resources.
According to researchers at MacKeeper, the campaign does not rely on exploiting specific software vulnerabilities. No common vulnerabilities and exposures (CVEs) have been identified. Instead, the attack chain exploits social engineering, brand familiarity and the implicit trust users place in both Google-hosted pages and Apple-like interfaces from Apple.
Security experts describe the operation as a macOS adaptation of older Windows-focused scams that promoted bogus “PC optimizers.” The technical elements—Base64 encoding, silent curl execution, and UI mimicry—are well known, but their combination within Google’s advertising and scripting infrastructure gives the campaign unusual reach.
Investigators also point to anomalies in advertiser behavior. Some accounts tied to the malicious ads run benign campaigns elsewhere, suggesting account takeover rather than outright creation by criminals. That pattern, coupled with the use of trusted domains like docs.google.com previews and Apps Script URLs, allows the ads to evade blockers and initial scrutiny.
For users, the warning from researchers is direct and specific: no legitimate macOS maintenance tool requires pasting opaque commands into Terminal. The appearance of routine system messages, they say, is precisely what makes the deception work.
Stay connected for insightful content that not only keeps you informed but also empowers you to navigate the dynamic world of cyber crime, cybersecurity, and digital safety!
© 2017 The420.in. All rights reserved. | Developed by Brainfox Infotech.